SAP System Security in Unix and Windows Platform Single Sign-On Concept So the security in SAP system is required in a distributed environment and you need to be sure that your data and processes support your business needs without allowing unauthorized access to critical information. BI Security Role Design.

Best Practice Sap Role Re Design Youtube
SAP SuccessFactors Learning Implementation Considerations for Efficient Security Design Implementation Design Principle documents are owned and managed by SAP SuccessFactors Product Management who.

. Tasks include SAP Security Role Design coaching less experienced SAP Analysts in the US and Bangalore making. Role Management is costly complex and fraught with risk. The transactional role also handles the authorization objects.
When you first implement SAP SuccessFactors Learning you need to think a little about the. Business processes and Role based Authorization Concept. In this module special care must be given to roles since the target population is external users of the system.
A good security design ensures that an organization can manage the proper authorization data privacy data integrity etc. Checkout Our Frequently Asked SAP Security Interview Questions. In an SAP HANA XS classic environment role developers create database roles as design-time objects in the built-in repository of the SAP HANA database using either the SAP HANA Web Workbench or the SAP HANA studio.
In a SAP system human errors negligence. This blog post introduces you to the recently published SuccessFactors Implementation Design Principle SFIDP document. The implementation of the new SAP security design helped this client reduce the number of roles in the SAP environment which combined with the SAP GRC Access Controls application facilitated the overall user provisioning processes.
Proficient with SAP authorization concept role design user administration SOD conflict resolution. Best practices and recommendations for developing roles in SAP HANA. But these are all mitigated with the Risk Management module from Security Weaver.
In an SAP HANA XS advanced environment role developers use the SAP Web IDE for SAP HANA to create the design-time version of roles within a project stored in the GIT repository. Implementing a strong Security strategy with policy adherence is requisite to manage compliance minimize risks and to setup a secure and efficient authorization concept with process efficiency and adoption which can be based on organizational structures. Roles in the SAP HANA database can exist as runtime objects only catalog roles or as design-time objects that become catalog objects on deployment database artifact with file suffix hdbroleIn an SAP HANA XS classic environment database roles are created in the built-in repository of the SAP HANA database using either the SAP HANA Web Workbench.
Learning does not use Role Based Permissions RBP but instead uses security domains roles and security permissions. Note SAP HANA XS classic and the SAP HANA repository are deprecated as of SAP HANA 20 SPS 02. This guides explains the new role development framework for SAP HANA using XS Advanced and HDI.
This model provides complete control and granularity for the privileges you want to grant to users. Best practices and examples for developing roles in SAP HANA. Role Management allows you to design document test approve track status automatically generate and automatically transported roles to targeted system.
The transaction and valuecontroller role concept deals with the design of individual transaction roles and authorization objects. Can somebody please provide the Role to T-Code matrix or any document to facilitate the role design workshops with BI Functional Teams which are starting next week. It gives recommendations and provides examples on how to best build roles.
Each privileged operation in a database requires one or more system or object-level privileges be assigned to the user to execute the operation. Please email at. Role-based permission is essential for the good security design of SAP SuccessFactors Onboarding solution.
The BPPs are used for building training and integration testing scenarios. Authorization objects deal with the final transaction access. You need to design the overall SAP security strategy based on the customer requirements.
Best practices and examples for developing roles in SAP HANALearn about building HDI containers and their setup create design-tiem objects in MDC and about granular roles adminstration roles security roles and support roles Download the Document. The following activities should be conducted. Our company is implementing BI 70 and I am responsible for creating the BI Security Role Designs.
The client to design and implement a new SAP security design following our tier 4 methodology. Strong knowledge in SAP Security tables and ability to efficiently and accurately identify authorization errors using SUIM SU53 and ST01 to provide consultative support to business. Transaction Value Roles.
The Security Matrix helps to view the roles in an easy-to-read format and helps the SAP Security Team communicate to the functional teams the security roles being configured. The functional teams can use the security matrix to assist in adding theroles to their BPPs business process procedures. Minimum 5 years experience in GRC 10.
When you implement SAP SuccessFactors Learning you assign security domains and security domain groups to roles to control who can access which features. When the developer deploys the project a runtime version of the roles is created in an HDI container schema within the SAP HANA database. SAP Security Architect will complete application security tasks covering all aspects of audit design testing and implementation of SAP roles through project work incidents and service requests.
SAP IQ provides a role-based security model for controlling access to database objects and executing privileged operations.
How To Build An Sap Security Role Matrix Www Brunocorreia Com

Identity Management And Sap Users Roles And Transactions Part1 Ibm Security Identity And Access
How To Build An Sap Security Role Matrix Www Brunocorreia Com

Sap S 4hana Authorizations Sap Blogs
How To Build An Sap Security Role Matrix Www Brunocorreia Com
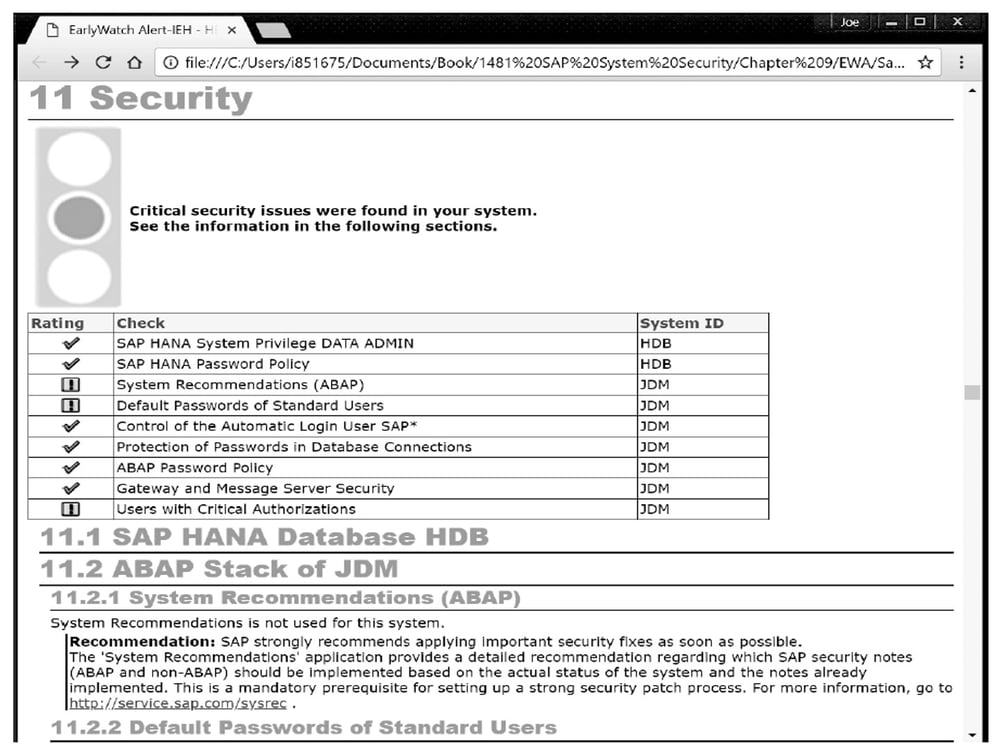
The Definitive Guide To Sap Security Sap Press
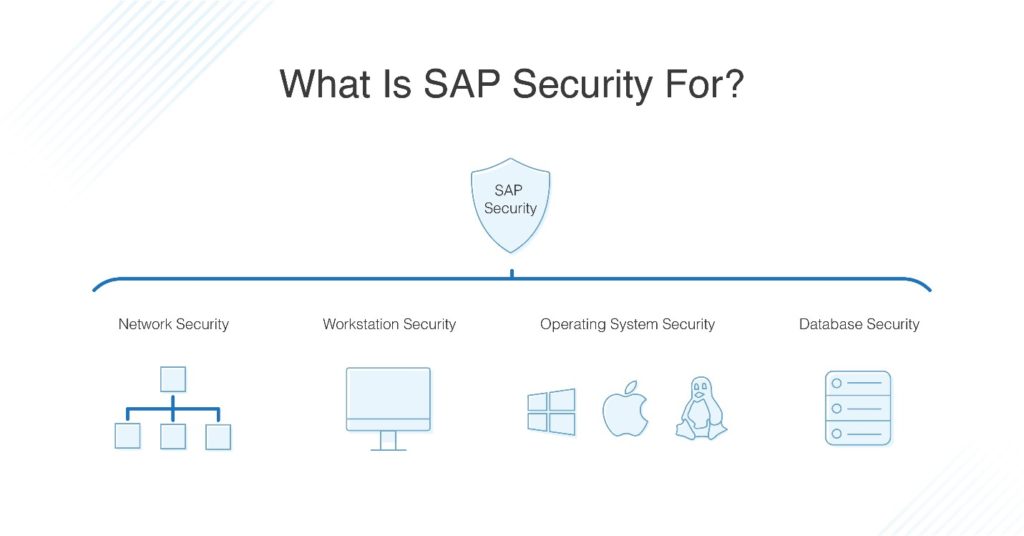
Sap Security Tutorial For Beginners Dnsstuff

Identity Management And Sap Users Roles And Transactions Part1 Ibm Security Identity And Access
0 comments
Post a Comment