The FBI is seeking victims whose personally identifiable information PII may have been misused between September 2018 and. The threat of identity theft is on the rise.
View Online_ID_theft_techniques_investigation_and_respopdf from CSE 4004 at VIT University Vellore.
. Ad Answer Simple Questions to Make An ID Theft Affidavit On Any Device In Minutes. Seeking Victims in Identity Theft Investigation. It can happen to anyonebut there are steps you can take to protect yourself and to recover if it happens to.
Get Protection from Identity Theft. Ad Best Identity Theft Protection Services 2022. Advantage Business Equipment - Check Signing Software Machines.
Identity theft has swiftly become a serious issue for victims police and prosecutors and is a problem that is requiring an increased commitment of resources by private enterprise. Ad IBM Fraud Prevention Provides a Seamless User Experience and Proves Continuous Compliance. Ad Learn How to Prevent Identity Theft and Fraud with 2022s Best-Value Protection Plans.
Online ID theft techniques investigation and response 77. The state with the highest per capita rate of. With the growth of technology protecting your personal information has never been more important.
The goal of this project was to enumerate their existing investigative techniques training programs and. Topics within identity theft. See discussions stats and author profiles for this publication at.
Ad Check Signing Software Machines Industrial Shredders and more. Compare Identity Theft Protection Reviews. For example training in identity theft usually involves providing investigators with the newest investigative techniques resources and victim-related issues.
Select Popular Legal Forms Packages of Any Category. Examples of how stolen personal information can be used to. Once someone has committed identity.
Fraudsters use a variety of techniques to acquire a victims card number. These techniques are listed under three headings. Guard Against Breaches of Lost or Stolen Credentials with Password Protection.
Ad Improve Visibility and Control Access with Adaptive Policies Based on Contextual Factors. Easily Customize Your ID Theft Affidavit. The keys to successfully investigating and actually solving an active identity theft case are Experience Expertise Technology and Reaction Time.
Get Protection from Identity Theft. The University of Glamorgan and is currently working towards a PhD in Data. See Why KuppingerCole Rates IBM as an Industry Leader in the Market for Fraud Reduction.
Identity theft occurs when someone uses your identity in a crime or fraudulent act. All Major Categories Covered. Mining of Intrusion Detection Systems.
Ad Instant Download and Complete your Amendments Forms Start Now. And 3 social engineering. Significant identity theft activity and large city police agencies in New York State.
As technology advances so do the techniques used by identity thieves. With a record number of victims in 2016 identity theft is becoming more prevalent in the United States and the growing trend will get worse before it gets better. There Are Many Ways to Prevent Identity Theft.
See our ID Protection Reviews Find Who Is Rated 1. Ad Best Identity Theft Protection Services 2022. Compare Identity Theft Protection Reviews.
These Companies Offer Inclusive Protection. Download Print Anytime. The number of people affected by identity theft grew by 500000 people from 126 million in 2012 to 131 in 2013 with escalating losses as well.
See our ID Protection Reviews Find Who Is Rated 1.

Pdf Identity Theft Identity Fraud And Or Identity Related Crime

Pdf Online Id Theft Techniques Investigation And Response

Tips And Advice To Prevent Identity Theft Happening To You Europol

Calameo Identity Theft Protect Your Identity Online
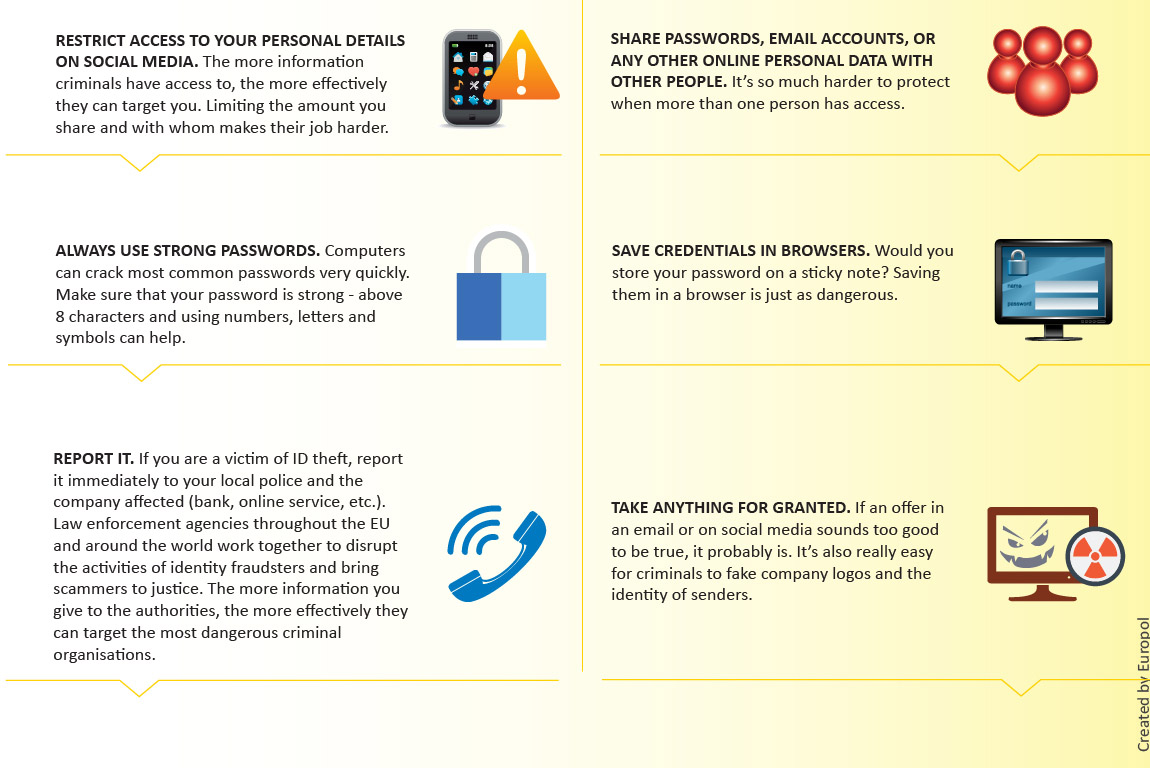
Tips And Advice To Prevent Identity Theft Happening To You Europol



0 comments
Post a Comment